
- Jan 6, 2025
- 30 min read
Backdoor attack? What is it?How does it work?
backdoor attack is an undocumented way to bypass existing cybersecurity measures and gain access to the computer system or device. Software and hardware developers sometimes install backdoors into their own products to retain access for troubleshooting purposes.
Backdoor installation helps software developers solve various problems, for example, retrieve data from a device to aid a criminal investigation or restore users’ lost passwords. But the backdoors might also be exploited by hackers, but how?
How does a backdoor attack work?
Backdoor attack works in two ways. Hackers might either discover and exploit a backdoor that already exists within a system, or they might install a backdoor into the system themselves.
In the first scenario, hackers use a backdoor to circumvent normal security measures and gain unauthorized access to a computer system and its data. In the second one, they exploit system vulnerabilities to gain access into it and implant backdoor software. Once the backdoor is in, attackers can easily re-enter the system whenever they like, even if the vulnerabilities are fixed.
Threat actors might use malware to set up an entry point into the system. When the malware infects the system, it brings in other harmful programs to make it possible to create a backdoor. For example, a rootkit infection can result in the creation of a backdoor in a system. Once the backdoor is set up, hackers send commands from a command-and-control server through this backdoor to steal data or damage the system.
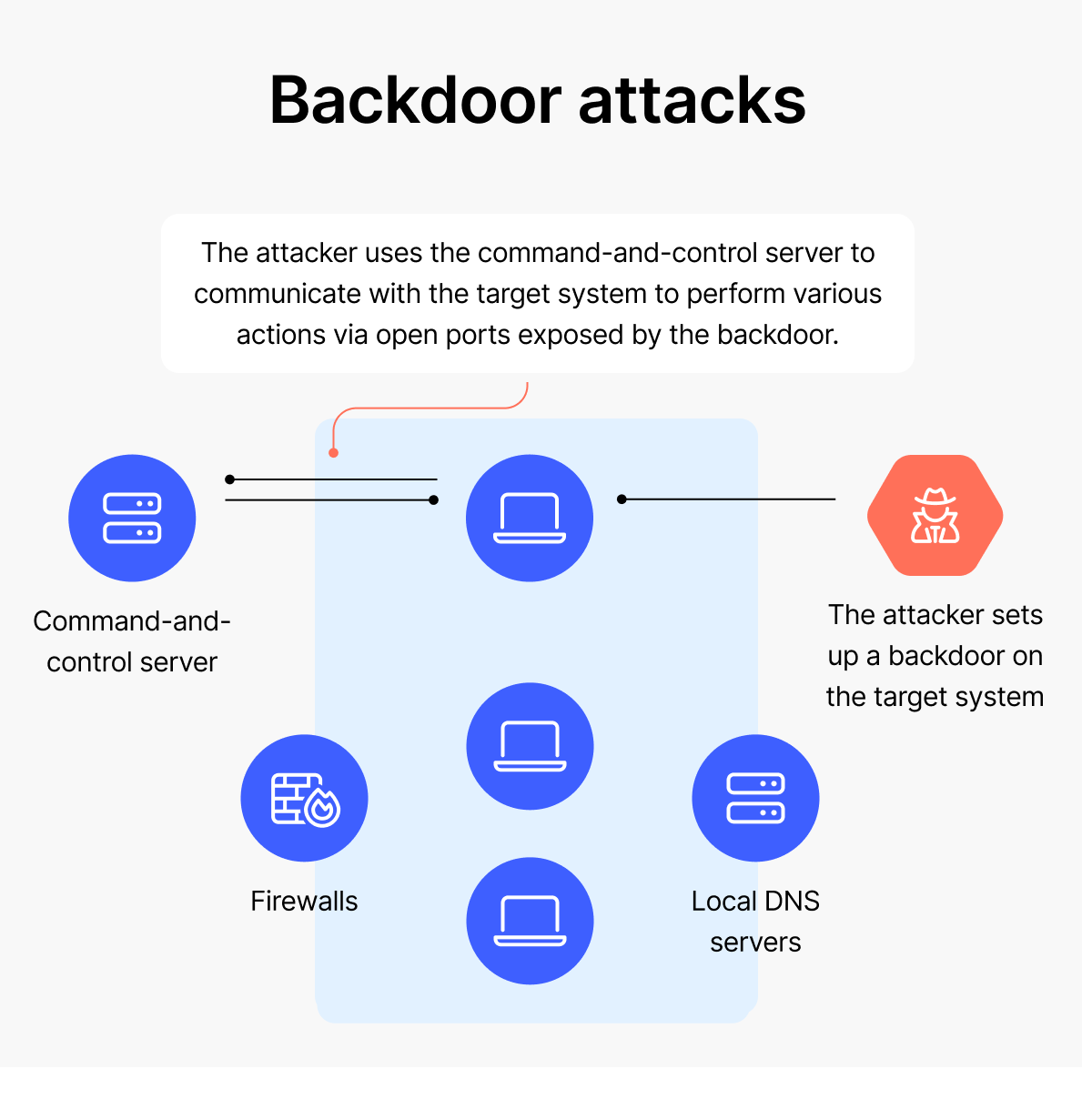
How does a backdoor attack work?
These attacks often go undetected, at least at first, because the hackers do not disrupt or brute force their way through any of the cybersecurity systems. Once they’ve got remote access to a network or device, they can install malware, engage in data theft, and spy on user activity.
How dangerous is it?
Backdoor attacks can be extremely dangerous because they often involve hackers gaining an extremely high level of access and privileges within a system or network. If they can do this without being detected, they can then squat there for months, monitoring user activity. Here are just some of the dangers posed by backdoor attacks.
- Massive data theft. If the backdoor attack has been successful, the hacker can ransack databases and steal private information.
- Spear phishing attacks. Hackers could use backdoors to access email accounts or other internal messaging systems within an organization and then send targeted phishing emails to the contacts of the compromised account. This may allow them to spread malware or backdoor trojans to other accounts.
- Cyber espionage. Backdoor attacks are the preferred strategy for cyber spies working on behalf of rival nation states. Unlike other forms of spying, these attacks don’t require physical access, so a successful backdoor hacker can spy on an enemy government from the other side of the world.
- Cyber warfare. While some hackers might just steal sensitive information, others could do a lot worse. Backdoor intrusions can allow state-backed hackers or even lone-wolf terrorists to carry out acts of cyber warfare. Power grids, water filtration plants, missile systems, and other important infrastructure essential for health and safety are all potentially vulnerable to backdoor attacks, and disruption in these areas could be catastrophic.


